推荐学习书目
› Learn Python the Hard Way
Python Sites
› PyPI - Python Package Index
› http://diveintopython.org/toc/index.html
› Pocoo
值得关注的项目
› PyPy
› Celery
› Jinja2
› Read the Docs
› gevent
› pyenv
› virtualenv
› Stackless Python
› Beautiful Soup
› 结巴中文分词
› Green Unicorn
› Sentry
› Shovel
› Pyflakes
› pytest
Python 编程
› pep8 Checker
Styles
› PEP 8
› Google Python Style Guide
› Code Style from The Hitchhiker's Guide
这是一个创建于 2352 天前的主题,其中的信息可能已经有所发展或是发生改变。
如图
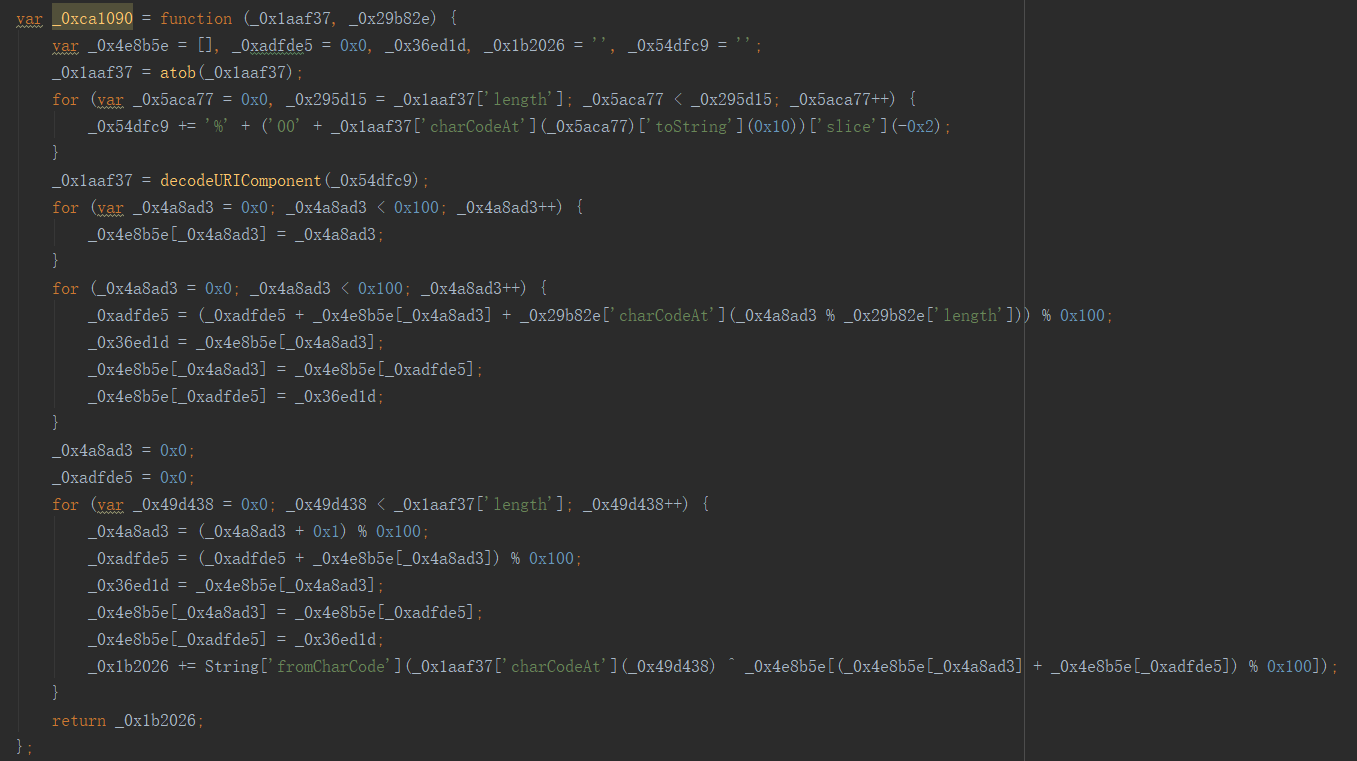
1
wly19960911 2019-07-19 11:20:46 +08:00 先把字符串都替换成短的,然后调试看输出和输入,之后确定 return 的值是怎么被改变的。这个还挺容易的。
|
2
zjsxwc 2019-07-19 11:25:21 +08:00 这是个脚本语言加密的思路,
其实只要简单地把变量名混淆以及把注释去掉之后, 就能让大部分人看不懂代码在干什么。 |
3
huaerxiela6 2019-07-19 11:27:02 +08:00 目测变种 rc4,不知道是不是 incapsula 的 cdn,如果是,可以通过简书联系到我
|
4
huaerxiela6 2019-07-19 11:27:38 +08:00
Incapsula cdn 破解: https://www.jianshu.com/p/4e1b466b26aa
|
5
wersonliu9527 OP |
6
MzM2ODkx 2019-07-19 12:04:30 +08:00
以前见过这种代码,不过没有深入研究过,在 chrome 的 source 里,鼠标移上去会显示真正的标识符,可以能是有个映射
|
7
sleepm 2019-07-19 13:09:30 +08:00 ```
var _0xca1090 = function(_0x1aaf37, _0x29b82e){ var _0x4e8b5e = [], _0xadfde5 = 0x0, _0x36ed1d, _0d1b2026 = '', _0x54dfc9 = ''; _0x1aaf37 = atob(_0x1aaf37); for( var _0x5aca77 = 0x0, _0x295d15 = _0x1aaf37['length']; _0x5aca77 < _0x295d15; _0x5aca77++){ _0x54dfc9 += '%' + ('00' + _0x1aaf37['charCodeAt'](_0x5aca77)['toString'](0x10))['slice'](-0x2); } _0x1aaf37 = decodeURIComponent(_0x54dfc9); for(var _0x4a8ad3 = 0x0; _0x4a8ad3 < 0x100; _0x4a8ad3++){ _0x4e8b5e[_0x4a8ad3] = _0x4a8ad3; } for(_0x4a8ad3 = 0x0; _0x4a8ad3 < 0x100; _0x4a8ad3++){ _0xadfde5 = (_0xadfde5 + _0x4e8b5e[_0x4a8ad3] + _0x29b82e['charCodeAt'](_0x4a8ad3 % _0x29b82e['length'])) % 0x100; _0x36ed1d = _0x4e8b5e[_0x4a8ad3]; _0x4e8b5e[_0x4a8ad3] = _0x4e8b5e[_0xadfde5]; _0x4e8b5e[_0xadfde5] = _0x36ed1d; } _0x4a8ad3 = 0x0; _0xadfde5 = 0x0; for(var _0x49d438 = 0x0; _0x49d438 < _0x1aaf37['length']; _0x49d438++){ _0x4a8ad3 = (_0x4a8ad3 + 0x1) % 0x100; _0xadfde5 = (_0xadfde5 + _0x4e8b5e['_0x4a8ad3']) % 0x100; _0x36ed1d = _0x4e8b5e[_0x4a8ad3]; _0x4e8b5e[_0x4a8ad3] = _0x4e8b5e[_0xadfde5]; _0x4e8b5e[_0xadfde5] = _0x36ed1d; _0x1b2026 += String['fromCharCode'](_0x1aaf37['charCodeAt'](_0x49d438) ^ _0x4e8b5e[(_0x4e8b5e[_0x4a8ad3] + _0x4e8b5e[_0xadfde5]) % 0x100]); } return _0x1b2026; } ``` ``` var func_1 = function(param_1, param_2){ var empty_array = [], start_at = 0, undefined_var, str_1 = '', wait_decode_uri = ''; param_1 = atob(param_1); // base64_decode for( var for_i_1 = 0, param_1_length = param_1['length']; for_i_1 < param_1_length; for_i_1++){ wait_decode_uri += '%' + ('00' + param_1['charCodeAt'](for_i_1)['toString'](16))['slice'](-2); } param_1 = decodeURIComponent(wait_decode_uri); for(var for_i_2 = 0; for_i_2 < 256; for_i_2++){ empty_array[for_i_2] = for_i_2; } for(for_i_2 = 0; for_i_2 < 256; for_i_2++){ start_at = (start_at + empty_array[for_i_2] + param_2['charCodeAt'](for_i_2 % param_2['length'])) % 256; undefined_var = empty_array[for_i_2]; empty_array[for_i_2] = empty_array[start_at]; empty_array[start_at] = undefined_var; } for_i_2 = 0; start_at = 0; for(var for_i_3 = 0; for_i_3 < param_1['length']; for_i_3++){ for_i_2 = (for_i_2 + 1) % 256; start_at = (start_at + empty_array[for_i_2]) % 256; undefined_var = empty_array[for_i_2]; empty_array[for_i_2] = empty_array[start_at]; empty_array[start_at] = undefined_var; return_value += String['fromCharCode'](param_1['charCodeAt'](for_i_3) ^ empty_array[(empty_array[for_i_2] + empty_array[start_at]) % 256]); } return return_value; } ``` 你的代码不全,而且,粘贴代码不是比传到图床再粘贴更简单么 ocr 出来缺太多了 问你要代码还需要等,几分钟自己敲好了。。。。 先把 16 进制的换了 再查找替换变量名 |
8
duan602728596 2019-07-19 17:26:06 +08:00 感觉是用 javascript-obfuscator 加密的
|